New Android banking trojan called "Sharkbot", its way of attack and how to defend
Malware? not the antivirus?
Antivirus app downloaded to prevent from hacking, but this app has been controversial as it has been found to be malicious malware that infiltrates users' mobile devices, manipulates banking applications, and remits assets to the outside.
"Sharkbot", a Trojan horse that first appeared in October 2021 and continues disturbing Google. These can be easily downloaded from the official Google Play Store, but it turns into malicious apps at some point after being installed on the user's smartphone.

What is Sharkbot?
Sharkbot is a new-generation Android banking Trojan discovered by the Threat Intelligence team of the security company Cleafy. Sharkbot masquerades as a mobile app or a commonly used app with common name and icon.

Sharkbot is known to use the work "Sharked" in the binary of the APK file, and once the malware is installed, it executes key logging, SMS message interception, overlay attack, and remote control commands. Thee apps were already downloaded by more than 15,000 users worldwide, with most victims believed to be in the UK and Italy. Google, of course, they quickly deleted these apps and announced that they took action on other apps presumed to be Sharkbot.
How did they trick Google?
Usually, the app must go through a pre-inspection process prior to registering an app on an official stores such as Google Play. However, Sharkbot has been registered as a safe app as if it were a safe application tricking Google. How did this happen?
According to the analysis, Sharkbot has a variety of anti-analysis functions which allows it to detect sandbox environment or adjust the triggering time of hacking. Above all, full-fledged malicious functions are additionally downloaded from external C&C servers. This is the reason that there were no problems found during the inspection of the Google Play Store.
It is very difficult to catch Sharkbot that has a domain generation algorithm (DGA) that can freely change external C&C domain and a geofence functions that deactivate malicious functions in a specific area.
How did Sharkbot get a permission from users?
The Sharkbot dpownloaded on the user's smartphone reveals it's malignity the moment it receives an external command. Sharkbot is similar to other malware such as TeaBot and UBEL, it displays malicious pop-ups that repeatedly ask for extensive permission to steal user's sensitive information. Sharkbot, like other similar malware such as TeaBot and UBEL, displays malicious pop-ups that repeatedly require extensive authorization to steal user's sensitive information.

Sharkbot will be able to get all the permissions (declared in the AndroidManifest file) needed to hack the banking app once accessibility permissions and services are activated by user.
Sharkbot then uses Android's accessibility service authority to display an overlaid window over a normal mobile banking app to induce the user to enter personal information, obtain the login credentials of the acquired bank app, and send them to a malicious server.

ATS (Automatic Transmission System) of the Sharkbot
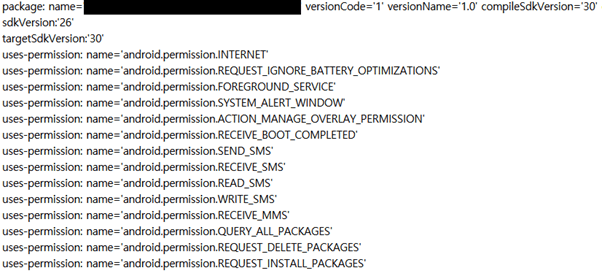
This information is used to access email, social media, online bank accounts, and more. With the permissions shown in the figure above, the Sharkbot can read or send text messages and perform overlay attacks. In particular, the REQUEST_IGNORE_BATTERY_OPTIMIZATIONS permission could bypass Android's doze component and connect to the C2 server to continue its malicious action.
Money is now transferred out of the victim's bank account. During this process Sharkbot can intercept the device's SMS messages and use them to get the 2FA sent by the bank. As attackers do not have to register new device for fraudulent activity, it is difficult to detect that money are being stolen even if the money is transferred from the victim's bank account.
The way how SharkBot avoids detection
SharkBot has a technology to avoid from anti-virus detection. It includes several features to avoid analysis and detection, such as inspecting and running emulators, encrypting command and control communication with remote servers, and hiding icons from the home screen after installation. Strings can be obfuscated to slow down static analysis and hide all commands and sensitive information used by the malware. Below is a list of other evasion features Sharkbot are using.
- Anti-emulator : It determines whether it is a real phone or an emulator when malware is installed on a device.
- External ATS module : The installed malware downloads additional modules from C2, and external modules are “.JAR” files that contain all the functions used to perform ATS attacks. This module is analyzed by Sharkbot in paragraph of the ATS module.
- Hide icon app : If malicious program is installed, Sharkbot hides from the app's icon from the device screen.
- Prevent deletion : Sharkbot uses accessibility services to prevent users from uninstalling the program from the setting options like other malware.
- Encrypted communication : All communication between the malware and C2 is encrypted and encoded with Base64, also use the domain generation algorithm (DGA).
How to detect and prevent Sharkbot?
While various security comapanies and stores are trying to defend themselves, it is no longer safe to trust such as APP Store and Google Play.
Users need to be alert now that malicious apps that try to hack into banking are constantly discovering new versions. This is why users should avoid installing apps that are unknown sources or that require excessive permissions, and periodically update legitimate antivirus to the latest version. In addition, it is important for individuals to carefully check the reviews, number of downloads and developer information each time downloading an app. It is also recommended to suspect and view apps that request permission for accessibility services unless there is a special case.
Companies that provide banking apps should take proactive steps to strengthen the security of the apps themselves and to detect&block malicious malware. LIAPP can detect apps known as Sharkbot through pattern detection. Also, LIAPP can prevent Sharkbot from hacking banking apps by performing functions such as overlay detection, remote control program detection, and screen capture program prevention. If you are a banking app service company, please contact the LIAPP team about Sharkbot. We will provide with more detailed consultation.
LIAPP, we provide the best service possible.
